… Unless I use a VPN.
I was recently on a wifi-enabled Southwest Airlines plane and before I was about to use it, I figured I’d look at how secure it actually was. To my disappointment, it was very easy to monitor the wireless traffic and would be effortless to compromise any number of the wireless users connected.
Keep in mind, I was only assessing the security to decide if it was safe for me to connect. The last thing I’d want is to get my credentials compromised because of my careless attention to security. While we send joke-emails around the office advertising that we’ll buy donuts when an employee’s computer gets ‘sharked’ (taken over by a passerby), I didn’t want to be an example of assuming the wifi on the aircraft is secure.
My access to my CRM and my company’s VPN yields an attacker access to millions of emails and business records. It’s a responsibility I take seriously. In a shared wireless wireless network, especially those lacking security, I do not connect. I am not going to cause another Target or Home Depot for my company.
Issue #1: Unencrypted Wi-Fi
The connection itself wasn’t encrypted. Even if we’re using a shared passphrase, the way WPA2 works is that the encryption key changes and is specific for each individual wireless client. It’s not that hard to use a passphrase. At the very minimum, it gives passengers a bit of assurance that security is valued to the airline operator. And to make sure every flight has a unique password, just append the flight number to the passphrase (like SWA1234) or a sponsor (like DishNetwork123). It would prevent automated, surreptitious monitoring of network traffic.
I know, informing passengers about the wireless password is so inconvenient, so why bother? Train your staff and educate them. Provide literature for passengers to understand the security risks and countermeasures you have employed.
Issue #2: Lack of AP Isolation
Okay, let’s assume that the wireless network was secure and our communication was encrypted. The next issue to address is enforce AP Isolation. The way that AP Isolation works is that at the router, it prevents any traffic from reaching any peers. Think of it like a virtual “quarantine” area that every connection is isolated from each other. Only connected to the router and no other peers. The router allowed me to connect and browse other machines and even conduct ARP poisoning since I was able to send broadcasts/multicasts to all other machines connected. This is a severe security risk to all users.
Unless people are using Chromecasts to stream video to other devices or share their iTunes libraries with other passengers, there is absolutely no reason to not enforce AP Isolation. It’s a basic feature in consumer routers, it should be available in your business-grade equipment. As an example, with AP Isolation enabled, I would not be able to see other wireless clients who are connected:
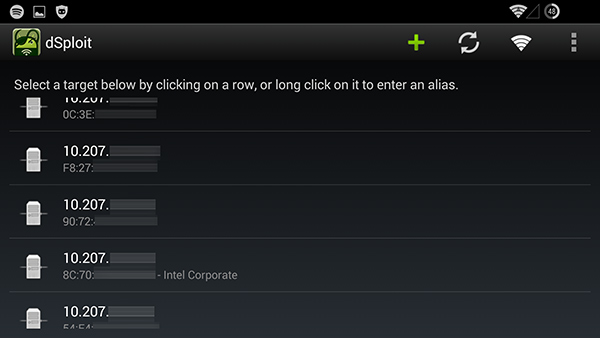
Issue #3: Insecure Payment Gateway
I didn’t recall seeing a valid (or invalid) certificate for the credit card payment page. I do recall that it was a self-signed certificate since all connectivity is disabled until a MAC address is authenticated. Given that a majority of users would experience broken and invalid SSL certs, it would be easy for someone to perform a MITM attack with SSLStrip and bounce all credit card details to the payment page. It seems very easy to conduct such an attack and do it stealthily.
And even those who didn’t pay for wireless internet, but only connected to the router are at risk. All one has to do is listen to acquire all the Facebook, Twitter, Amazon or even Gmail login attempts that occur with and without the user knowing. Advertising a self-signed certificate will train users to accept these willingly even though they are inherently unsafe.
It wouldn’t be a bad idea to add root Certificate Authorities to a whitelist of approved always-on connections so users can ascertain that they are connected to the page properly and that no one is eavesdropping.
Issue #4: HTML/Javascript Injection
As if connecting to an unencrypted wireless router, ability for others to monitor your connections and accepting self-signed SSL certs weren’t enough to give you the shivers, users are subjected to an invasive manipulation of their web traffic. For “convenience,” it appears that Southwest Airline adds a bit of Javascript that modifies your websites so you can easily logout. This injection is unsafe because if your router can do it, so can anyone else. And if someone can modify the output of websites that you browse, they can easily embed malicious scripts that can install malware or worse, rootkits, silently without any user interaction.
While I didn’t experience this myself, the possibility for it is there. According to other users, it appears Southwest injects an iframe into web pages while browsing on their wireless internet. The purpose of these injections in your web experience is intended so you can logout of them. It disables connectivity to your IP or MAC address on-demand when a user clicks the link. (Just a guess…)
Alternatively, this can be accomplished with a popup at login or after 15 minutes of idle activity. Injection isn’t needed unless there are plans to start delivering advertising.
Real-World Security Implications
Okay, I’ve outlined at least four issues why I won’t use the wireless internet provided by airlines. But, I know what you’re thinking, “Joe, if I’m not doing anything wrong, why should I care?” Security is not only a privilege given to criminals. It is everyone’s responsibility and we should expect it — especially when we pay for wireless internet services. Sure, when connecting to free wifi, it’s buyer-beware. On paid wireless internet, we all should expect reasonable, basic computer security precautions to be exercised.
So, here are some practical scenarios that affect nearly everyone:
- Corporate Espionage – Knowing about the current company crisis or upcoming launches can be valuable to your competitors. Perhaps access credentials to your customer databases would be a nightmare. One could acquire such information in just a matter of seconds once they are able to gain access to your email or computer. An attacker may hold your information hostage, demanding a ransom or would offer to sell it secretly to your competitors. (Or both.)
- Stalking – Maybe you had an abusive ex. Perhaps your ex has hired a private investigator to tail you. They could monitor your communications and uncover your destination, your contacts and even compromise your device giving them unfettered access to your data and whereabouts.
- Spear Phishing – It’s amazing how much information people transmit automatically about themselves. One could identify a high-value target and gather information about them, then deliver a specific and tailored phishing attack. Your devices and websites you use give attackers a lot of valuable information. Similarly, this information could be used for social engineering.
- Malware Distribution – We all know everyone is going to try to visit Google, Facebook, YouTube or other high-volume websites. You could just as easily embed a script that loads on your target’s machines. This malware could then spawn a rootkit, ultimately joining a botnet. Trust me, no flight attendants would know why a passenger is complaining about their machine suddenly becoming slow, hot, 100% CPU usage and 80% of their network utilized.
- Spam – Before passengers land, one could compromise their social network credentials and post information to their feeds promoting the latest and greatest product. Then hours or days later, they’ll hear about it and remove it. But the attacker will be long-gone and you’ll need to reset all your security credentials.
- Insecure Communications – In general, people are curious about your data. Anything that might be of no value to you, could be valuable to them. Perhaps updating your blog seems innocent enough, but to an attacker, it’s a goldmine of traffic and user information. Checking your company’s email – this could be valuable in case they want to conduct a “stranded tourist” attack on your employer or friends.
- National Security – I hate to even suggest this, but an attacker can compromise your communications and computer and issue a national security threat through your machine. Guess who’s going to get tackled by 25 agents when you land? Not the attacker– you will. And this distraction may delay law enforcement from actually identifying the attacker.
In only 90 seconds, I was able to acquire my Instagram, Amazon and personal website credentials with relatively simple attack methods. The only impact was that my internet connection briefly dropped but reconnected seconds later. Would you think otherwise if your internet was disconnected?
The solution?
Ultimately, the long-term solution is for commercial airlines like Southwest to secure their wireless internet offerings. For passengers, it’s crucial to use a VPN to secure your communications. For the price of pennies a day, you could secure yourself by encrypting and routing your connection even while on public wireless internet. Maybe it wouldn’t be a bad idea if Southwest offered passengers free/affordable VPNs to compliment their internet offering.
Also, the solution is to make sure you disable your wireless radio on your laptop or phone when you are not using it. Many devices, by default, connect to open networks trying to save you on cellular data usage. But all it takes in that process is a second to reveal all your active connections and identities.
Final Thoughts
I don’t write this to scare you. I don’t write this to complain about Southwest Airlines. In fact, I love them, like their brand and their generosity in providing internet service for its passengers.
I do write this to educate you and others about the risks of using someone else’s internet, especially wireless internet offered by airlines. I presume a lot of people travel for business and there could be some serious security risks in doing so. And when thinking of this from a security point of view, there is none. When you accept that and adjust your behavior (by employing countermeasures), you will be better protected from it.
Image credit: Washington Post